A Complete Pill for the Sage SmartProbe.
Note: Please read the FAQ!!!
The Sage SmartProbe was a very spiffy "Hard ICE" debugger, one of the few ever manufactured for use with modern (2010s) AMD x86-64 processors, and - as far as I'm aware - the only one ever sold on the mass market, rather than as part of "favourite son" deals (as, e.g., Intel's, and Arium's similar products were, and perhaps still are.)
Quite a few of these things ended up bundled with various dev boards, saddled with time-limited demo expiration (yes, a time-limited hardware peripheral! don't ask me...) The vendor perma-re-enabled an expired probe for a small fee.
Sage Eng. LLC, it appears, is long dead. Leaving no trace! How and why it died is unknown to me.
So now, instead of being unique tools in the development of, e.g., Coreboot, or whatever other attempts at sane utilization of x86-64 iron, the demo probes are stuck in limbo, working as so many peculiar paperweights.
This is a crying shame. Now you cannot unbrick the expired probes for any price. (At least not by buying the magic code from the original maker...)
So, without further delay, let us get one of these patients onto the operating table:
Now you could connect the thing to your favourite OpenOCD-compatible JTAG probe, and play around with the internals. E.g., this GDB script will give you an instruction trace. There are many interesting things to be learned, re: the command set (most of which is GDB-compatible, but there are a few interesting sharp edges.)
Or you could skip straight to the pill:
sage_pill.py
(SHA256: 2f9ce44fe069705a7ee83c0f4c733a6a0cc374613429c5c1f47a8481aa464b60)
1) Download the pill and the fw image.
2) Check the SHA256 sums.
3) Unpack the firmware image.
4) Plug in the probe.
5) ./sage_pill.py sage_last_public_fw.bin /dev/ttyACM0
You may have ended up with some device other than ttyACM0 when you plugged it in. Find out which.
The script will need to run with sufficient privileges to talk to the "modem".
It will ask for a final confirmation prior to firing.
6) Enjoy a 100% working x86-64 "Hard ICE".
This article is continued here.


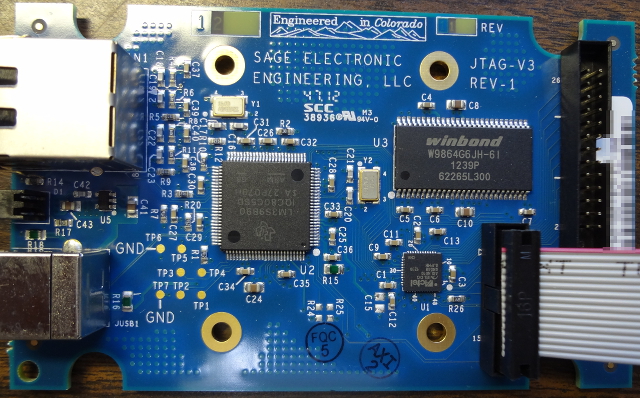
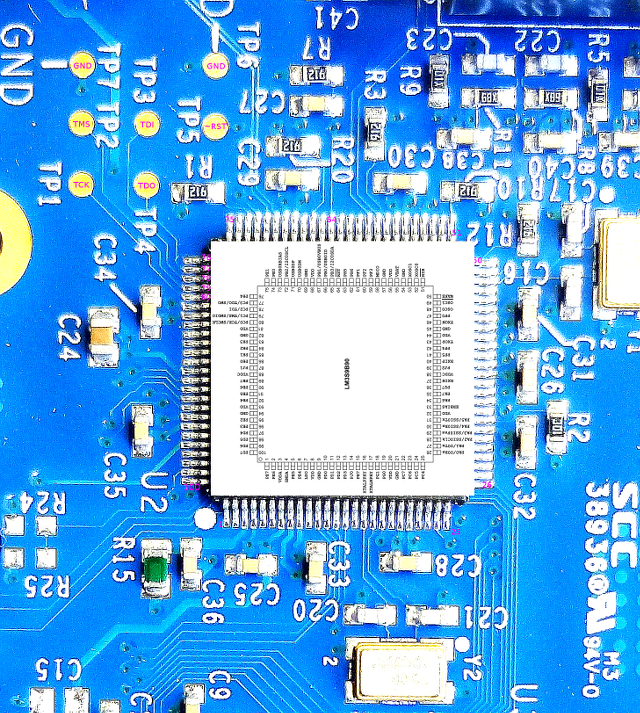


Hello, Download links are broken. Need help with that. Thanks.
Dear Printa,
The box where these lived, was recently destroyed, and there is not yet a permanent replacement.Ask politely on #trilema for a copy.It's back.Yours,
-Stanislav
Hi there,
I am trying to figure out the device name of the FPGA on the board below the SDRAM - but my eyes don't work too well! Would you happen to ahve the device number or a higher resolution photo of the area where the Actel chip resides?
Thanks!
Dear SquintyEyes,
It's an Actel "Igloo". See here.
Yours,
-S
Hello again,
Would you happen to have a high resolution photo of the back of the board?
Thanks!